The Science behind Sniffing Attack
Introduction
For the education on information security, one of the most fundamental topics is the common network attack called Sniffing attack. To collect confidential and sensitive information, by spying the network traffic, the sniffing attack is usually used by attackers. With the objective of enhancing information security education, this article discusses what fundamental security concepts and hands-on skills the students need to know and acquire about network sniffing attack, respectively. The process in which the data packets are monitored and captured that are passed through a computer network by using packet sniffers is called Sniffing. To keep track of data traffic passing through a network, the network administrators use the packet sniffers. Similarly, to capture data packets in a network, the use of these packet sniffing tools is employed by malicious attackers.
What is sniffing?
Sniffing is the process of monitoring and capturing data packets passing through a given network using software or hardware devices. At a high level there are two types of sniffing viz., active and passive. Active sniffing refers to sniffing on a switch-based network whereas Passive sniffing refers to sniffing on a hub-based network.
Working of sniffing attack
Predominantly sniffing is accomplished by the usage of sniffers. A sniffer turns the NIC of a system to the promiscuous mode so that it listens to all the data transmitted on its segment.
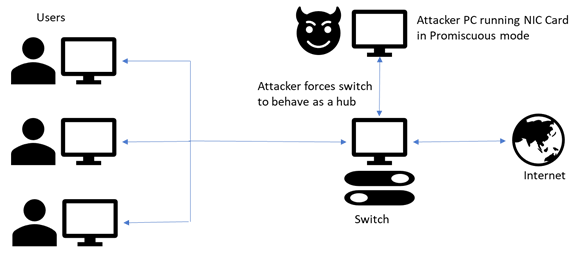
Types of sniffing attacks
As mentioned earlier, there are two main types of Sniffing.
· Passive Sniffing
o Passive sniffing refers to sniffing through a hub, where in the traffic is sent to all ports
o It involves monitoring packets sent by others without sending any additional data packets in the network traffic
o In a network that use hubs to connect systems, all hosts on the network can see all the traffic and therefore, the attacker can easily capture traffic going through the hub
o Hub usage is an outdated approach. Most modern networks now use switches
o Passive sniffing provides significant stealth advantages over Active sniffing

· Active Sniffing
o Active sniffing is used to sniff a switch based network
o Active sniffing involves injecting address resolutions packets (ARP) into the network to flood the switch’s content addressable memory (CAM) table, which keeps track of host — port connection.
o Some of the Active Sniffing techniques are
§ MAC flooding
§ DNS poisoning
§ ARP poisoning
§ DHCP attacks
§ Switch port stealing
§ Spoofing attack
Protocols Vulnerable to Sniffing
· Telnet and Rlogin — Keystrokes including user names and passwords are sent in clear text
· HTTP — Data is sent in clear text
· IMAP — Passwords and data are sent in clear text
· SMTP and NNTP — Passwords and data are sent in clear text
· POP — Passwords and data are sent in clear text
· FTP — Passwords and data are sent in clear text
Attack implementations in the network
· Workflow of how an attacker hacks the network using sniffers
- An attacker connects his laptop to a switch port

2. He runs discovery tools to learn about network topology

3. He identifies victim’s machine to target his/her attacks

4. He poisons the victim machine by using ARP spoofing techniques

5. The traffic destined for the victim machine is redirected to the attacker

6. The hacker extracts passwords and sensitive data from the redirected traffic

Sniffing in the Data Link Layer of the OSI Model
o Sniffers operate at the data link layer of the OSI Model
o Networking layers in the OSI model are designed to work independently of each other, if a sniffer sniffs data in the data link layer, the upper OSI layer will not be aware of the sniffing

Popular sniffing techniques and methods
· Hardware Protocol Analyzers
o A hardware protocol analyzer is a piece of equipment that captures signals without altering the traffic in a cable segment
o It can be used to monitor network usage and identify malicious network traffic generated by hacking software installed in the network
o It captures a data packet, decodes it, and analyzes its content based on certain predetermined rules
o It allows the attacker to see individual data bytes of each packet passing through the cable
o Some of the key hardware protocol analyzers in the market are N2X N5540A Agilent protocol analyzer, Keysight E2960B, RADCOM PrismLite protocol analyzer, STINGA protocol analyzer, NETSCOUT’s OneTouch AT Network Assistant, NETSCOUT’s Opt/View XG Network Analysis Tablet, Agilent Technologies 8753ES
· SPAN port — It is a port that is configured to receive a copy of every packet that passes through a switch. When connected to the SPAN port, an attacker can compromise the entire network

· Wiretapping — It is the process of monitoring telephone and internet conversations by a third party. Attackers connect a listening device such as hardware, software, or a combination of both to the circuit carrying information between two phones or hosts on the internet. It allows an attacker to monitor, intercept, access, and record information contained in a data flow in a communication system. Active wiretapping monitors, records, alters and also injects data into the communication or traffic. Passive wiretapping only monitors and records the traffic and collects knowledge of data it contains. In most countries, wiretapping without a warrant or the consent of the concerned person is a criminal offense.
· Lawful Interception — It refers to legally intercepting data communication between two end points for surveillance on the traditional telecommunications, voice over internet protocol (VoIP), data and multiservice networks.
· MAC Flooding — MAC flooding involves flooding of CAM table with fake MAC address and IP pairs until it is full. The switch then acts as a hub by broadcasting packets to all machines on the network and therefore, the attackers can sniff the traffic easily. A macof is a Unix / Linux tool that is a part of dsniff collection. The macof sends random source MAC and IP addresses. This tool floods the switch’s CAM tables by sending bogus MAC entries.

· Switch Port Stealing
o MAC flooding is used by Switch port stealing sniffing technique to sniff the network packets.
o Attackers flood the switch with forged gratuitous ARP packets with target MAC address as source and her own MAC address as destination.
o A race condition of attacker’s flooded packets and target host packets occur and thus switch has to change its MAC address binding constantly between two different ports.
o IN such case if attacker is fast enough, she will be able to direct the packets intended for the target host toward her switch port.
o Attacker now manages to steal the target host switch port and sends ARP requests to stolen switch port to discover target hosts’ IP address.
o When attacker gets ARP reply, this indicates that target host’s switch port binding has been restored and attacker can now sniff the packets sent toward targeted host.

· DHCP Starvation Attack and Rogue DHCP Server Attack
o The DHCP Starvation attack is a denial of service (DoS) attack on the DHCP servers where attacker broadcasts forged DHCP requests and tries to lease all of the DHCP addresses available in the DHCP scope. Therefore, the legitimate user is unable to obtain or renew an IP address requested via DHCP, failing access to the network access.
o Where as in the Rogue DHCP server attack, attacker sets rogue DHCP server in the network and responds to DHCP requests with bogus IP addresses resulting in compromised network access. This attack works in conjunction with the DHCP starvation attack; attacker sends TCP / IP setting to the user after knocking him / her out from the genuine DHCP server
· ARP Spoofing Attack
o Before understanding the ARP spoofing attack, it is important to first understand about ARP. Address Resolution Protocol (ARP) is a stateless protocol used for resolving IP addresses to machine addresses (MAC). All network devices that needs to communicate on the network broadcasts ARP queries in the network to find out other machines’ MAC addresses. When one machine needs to communicate with another, it looks up its ARP table. If the MAC address is not found in the table, the ARP_request is broadcasted over the network. All the machines on the network will compare this IP address to their MAC address. If one of the machine in the network identifies with this address, it will respond to ARP_request with its IP and MAC address. The requesting machine will store the address pair in the ARP table and bengin with the communication.
o In the ARP spoofing attack, the ARP packets can be forged to send data to the attacker’s machine. ARP spoofing involves constructing a large number of forged ARP request and reply packets to overload a switch. Switch is set in forwarding mode after ARP table is flooded with spoofed ARP replies and attackers can sniff all the network packets. Attackers flood a target computer’s ARP cache with the forged entries, which is also known as poisoning.
o The threats of ARP poisoning are packet sniffing, session hijacking, VoIP call tapping, data manipulation, man in the middle attack, data interception, connection hijacking, connection resetting, stealing passwords, denial of service attack (DoS).
· MAC Spoofing or Duplicating — This attack is launched by sniffing a network for MAC addresses of clients who are actively associated with a switch port and re-using one of those addresses. By listening to the traffic on the network, a malicious user can intercept and use a legitimate user’s MAC address to receive all the traffic destined for the user. This attack allows an attacker to gain access to the network and take over someone’s identity on the network.
· IRDP Spoofing — ICMP router discovery protocol (IRDP) is a routing protocol that allows host to discover the IP addresses of active routers on their subnet by listening to router advertisement and soliciting messages on their network. Attacker sends spoofed IRDP router advertisement message to the host on the subnet, causing it to change its default router to whatever the attacker chooses. This attack allows attacker to sniff the traffic and collect the valuable information from the packets. Attackers can use IRDP spoofing to launch man in the middle, denial of service and passive sniffing attacks.

· DNS Poisoning Techniques — It is a technique that tricks a DNS server into believing that it has received authentic information when, in reality, it has not received any. It results in substitution of a false IP address at the DNS level where web addresses are converted into numeric IP addresses. It allows attacker to replace IP address entries for a target site on a given DNS server with IP address of the server he controls. Attacker can create fake DNS entries for the server containing malicious content with names similar to that of the target server.
Sniffing Tools
Wireshark: Helps to capture and interactively browse the traffic running on a computer network. It users Winpcap to capture packets on its own supported networks. It captures live network traffic from Ethernet, IEEE 802.11, PPP / HDLC, ATM, Bluetooth, USB, token ring, frame relay, FDDI networks. A set of filters for customized data display can be refined using a display filter.
SteelCentral Packet Analyzer: It provides a graphical console for high speed packet analysis
Capsa Network Analyzer: Capsa network analyzer captures all data transmitted over the network and provides a wide range of analysis statistics in intuitive and graphic way
OmniPeek: OmniPeek sniffer displays a Google Map in the OmniPeek capture window showing the locations of all the public IP addresses of captured packets
Observer Analyzer: Observer provides a comprehensive drill-down into network traffic and provides back in time analysis, reporting, trending, alarms, application tools, and route monitoring capabilities.
PRTG Network monitor: General purpose
CommView: General purpose
CSniffer: A product from McAfee
Colasoft Packet builder: General purpose
NetResident: General purpose
EtherApe: General purpose
RSA NetWitness investigator: A product from RSA
Ntopng: General purpose
Network probe: General purpose
Tcpdump: Used by most of the ethical hackers
SmartSniff: General purpose
WebSiteSniffer: General purpose
NetFlow Analyzer: General purpose
Free Network Analyzer: General purpose
Kismet: Used by most of the ethical hackers
Identifying the Sniffer
Following are some of the common methods to identify or detect the sniffers.
· Ping method — Sends a ping request to the suspect machine with its IP address and incorrect MAC address. The ethernet adapter rejects it, as the MAC address does not match, whereas the suspect machine running the sniffer responds to it as it does not reject packets with a different MAC address.
· DNS method — Most of the sniffers perform reverse DNS lookup to identify the machine from the IP address. A machine generating reverse DNS lookup traffic will be most likely running a sniffer.
· ARP method — Only a machine in promiscuous mode (machine c) caches the ARP information (IP and MAC address mapping). A machine in promiscuous mode responds to the ping message as it has correct information about the host sending the ping request in its cache; rest of the machines will send ARP probe to identify the source of ping request.
Motives behind sniffing
· To steal the username and passwords for financial benefits
· To steal the victim’s bank account and transaction details
· To spy the chat messages, personal conversations and email communication messages
· To steal personal identity for various benefits
Sniffing defending and prevention techniques
· Restrict the physical access to the network media to ensure that a packet sniffer cannot be installed
· Use end to end encryption to protect confidential information
· Permanently add the MAC address of the gateway to the ARP cache
· Use static IP addresses and ARP tables to prevent attackers from adding the spoofed ARP entries for machines in the network
· Turn off network identification broadcasts and if possible restrict the network to authorized users to protect network from being discovered with sniffing tools
· Use IPv6 instead of IPv4 protocol
· Use encrypted sessions such as SSH instead of Telnet, Secure Copy (SCP) instead of FTP, SSL for email connection, etc. to protect wireless network users against sniffing attacks
· Use HTTPS instead of HTTP to protect user names and passwords
· Use switch instead of hub as switch delivers data only to the intended recipient
· Use secure file transfer protocol (SFTP), instead of FTP for secure transfer of files
· Use PGP and S/MIME, VPN, IPSec, SSL//TLS, Secure Shell (SSH) and one time passwords — OTP
· Always encrypt the wireless traffic with a strong encryption protocol such as WPA and WPA2
· Retrieve MAC directly from NIC instead of OS; this prevents MAC address spoofing
· Use tools to determine if any NICs are running in the promiscuous mode
· Use a concept of ACL or Access Control List to allow access to only a fixed range of trusted IP addresses in a network
· Port Security can be used to restrict inbound traffic from only a selected set of MAC addresses and limit MAC flooding attack
· Enable DHCP snooping that allows switch to accept DHCP transaction directed from a trusted port
· Implement Dynamic ARP inspection using DHCP snooping binding table to defend against ARP Poisoning
· Implement Domain Name System Security extension (DNSSEC), restrict DNS recusing service, either full or partial, to authorized users.
· Audit your DNS server regularly to remove vulnerabilities
